Have you ever wondered how digital transformation can unlock new opportunities for us and make things better? We are living in the 21st century which is fully science-based, but what will happen to those who are not adapting to these technologies?
Former CEO of Cisco John T. Chambers said, “At least 40% of all businesses will die in the next 10 years if they don’t figure out how to change their entire company to accommodate new technologies.” This statement pretty much made it clear how important it is to incorporate mode day tech with your business, just as it’s important for employees to understand what does year to date mean on a pay stub, ensuring they grasp essential financial details.
But digital transformation can’t help us until we have a secure and strong system of foundations. Old/outdated systems aren’t going to take us anywhere with the business operations, so what can be done?
In this article, we’ll talk about how companies and businesses can make their own secure systems and access the full potential of technology infrastructure.
Understanding Technology Infrastructure
Technology infrastructure includes interconnected enterprise hardware, software, and networking technologies supporting business-critical systems accessed securely daily, including:
- Hardware – Servers, data centers, workstations, mobile devices, and networking switches represent physical networks, maintaining digital environments and remote access capabilities securely.
- Software – Centralized software platforms like customer relationship management, document management systems, and customized line-of-business applications prove foundational in tracking all essential functions and translating raw data into actionable business insights. Based on the article of TechTarget as well, mission-critical applications must be maintained to ensure continuous operations.
- Networks – Local area networks, wireless connectivity, comprehensive area network links, software-defined perimeters, and virtual private network access protocols connect locations and devices, permitting secured accessibility remotely by workforce populations fluidly as needed securely.
Optimizing system architecture directly fortifies organizational efficiency through:
- Improving productivity and responsiveness by sensing real-time shifts via performance monitoring and automation translates instantly into actions everyone takes decisively.
- Reducing business continuity risks that infrastructure failures threaten daily through modernizing antiquated servers, reinforcing network security patches promptly, plus support strategies assisting teams in keeping essential systems available 24/7.
- Lowering data liability exposures via stringent access controls, network micro-segmentation, and multifactor authentication verifies users stringently before granting data generous data privileges feared exploited otherwise initially.
Well-architected technology foundations empower enterprises to react to market dynamics rapidly, gaining competitive advantages, seizing opportunities forward, and surpassing competitors struggling with change weighed down by fragmented environments.
Conducting an Infrastructure Assessment

Documenting existing technology setup fully gives operational leaders accurate inventories detailing complete hardware and software assets deployed, current configurations, and vital systems interdependencies that keep organizations functioning daily. This baseline insight then reveals:
- End-of-life equipment lacking modern security protections risks exposing network vulnerability unnecessarily until it is upgraded reasonably.
- Overlooked single-points-of-failure where operations rely on singular servers/devices that, when offline, incur business shutdowns that redundancy solutions mitigate quickly and cost-effectively.
- Streamlining opportunities consolidating duplicated applications overlapping functions better integrated to improving workflows efficiently long term after short-term transitional pains subside, adoptions completed organization-wide cross-departmentally.
Key areas for assessment
Infrastructure evaluations focusing on security, complexity, and future scalability surface actionable evidence improving essential technology capacities maximized protecting enterprises now and through disruptions inevitably ahead persists at a pace unrelenting continuously.
- Security – Hardening protocols, upgrading old platforms, and centralized monitoring represent ongoing safeguard imperatives as gaps manifest daily and are exploited easily by automated bots probing relentlessly, seeking what underprepared neglects, leaving visible or worse undetected.
- Complexity – Interdependencies risk unraveling operations if neglected. Documenting and diagram detailed connectivity mapping followed simplifying convoluted application portfolios through workflow integrations over add-on band-aids stretched capabilities temporarily alone but backfired scaling up exhibiting platform cracks exposed woefully later.
- Compatibility – Assessing current built-in capacity supporting current and planned expansions ensures responsively adjusting server resources, networking throughput, and platforms seamlessly, keeping performance optimally amidst growing pains onlookers notice minimally.
Recommended tools and methodologies for assessment

Informed evaluations utilize a combination of top-down and bottom-up analyses revealing enterprise digital infrastructure’s actual standing qualitatively and quantitatively. Tactics include:
- SWOT Analysis – Strategic framework identifying strengths, weaknesses, opportunities, and threats that keeps executive planning updated responsively over traditional lagging indicators alone that proves woefully unreliable narrating how fast market dynamics changes continuously go now.
- IT audits and assessments – Documenting exhaustive inventories assessing integrated systems interdependencies risks uncovers critical components that, when breached or failed, threaten overall operational continuity through cascading disruptions difficult arresting once gain uncontrollably unknowingly.
To put this into perspective, Seattle IT support experts help businesses take advantage of comprehensive IT assessments. They identify risks associated with outdated hardware while streamlining complexities across installed software, data security, and networking capacities.
This approach sustains responsive performance, which might otherwise be feared lost due to operational disruptions, but can be proactively prevented by optimizing digital environments. Ultimately, this maximizes productivity and ensures uninterrupted business functions.
Strategies for Simplifying Technology Infrastructure
Everything needs to be continuously supported to prevent the challenges that come with increasing complexity. As systems grow, overlapping functionalities can become a burden, making maintenance more difficult.
That’s why it’s essential to have flexible scalability through smart solutions that streamline operations and keep everything running smoothly.
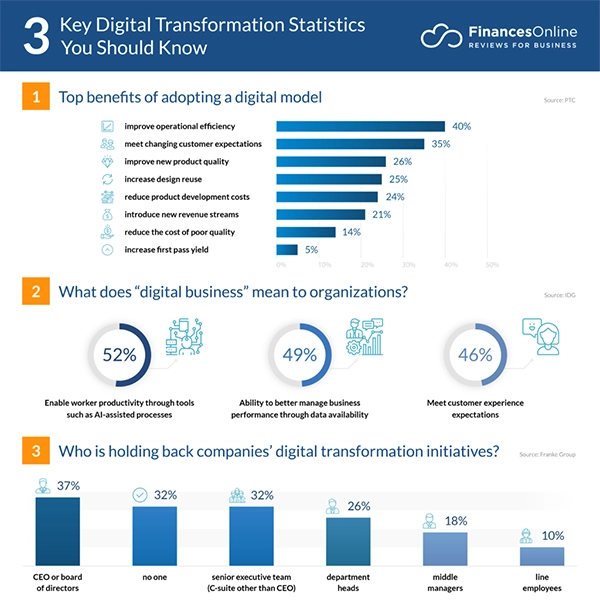
For your better understanding, look at the stats below showcasing key statistics related to digital transformation.
Streamlining software and applications
Focusing on platform integration helps ensure that different systems work together seamlessly. This allows for smooth automation and easy sharing of data across departments.
Once these functionalities are combined with standard interfaces and permissions, it prevents workflow bottlenecks that can arise when sharing data becomes necessary but is difficult to set up later on. By prioritizing integration from the start, we can avoid the pitfalls of short-sighted planning.
Leveraging cloud technologies
Transitioning suitable operations to a secure cloud infrastructure can significantly lighten the load of managing uptime. By relying on cloud providers, businesses can benefit from the automatic scaling of server capacities.
This means that whenever demand peaks, pre-configured alerts will notify the provider to add resources dynamically, ensuring that you only pay for what you use during those busy times.
This approach is often more cost-effective than traditional licensing contracts that require ongoing payments for unused capacity, which can lead to unnecessary expenses.
Implementing automation in business processes
Repeatable manual processes automated intelligently save thousands of redundant hours, reassigning skilled talent innovating new products and offerings competitively differentiating brand reputations further by competitors struggling to play catch-up continually.
Enhancing Security Measures
Hardening protective measures and combatting intensified advanced cybercrimes requires implementing resilient safeguards through frameworks technologies and workforce preparedness supporting coordinated responses, minimizing enterprise-wide cyber disruptions when breaches inevitably occur statistically predicted annually.
Understanding Key Threat Vectors
Whether internally accidental, externally criminally motivated, or state-sponsored advanced persistent groups, common tactics include:
- Ransomware attacks encrypt access locally or backups remotely, halting operations hostage until demands for payments are met criminally.
- Business email compromises infiltrate commercial communication chains, requesting false payments or data transfers that appear legitimately by impersonation authority initially until too late, uncovering schemes unraveling wreckages left behind painfully.
- Insider threats recruitments targeting sympathizers radicalized politically leaked confidentialities, deleted essential records, or data theft CNP personally gains realized illegally.
- Supply chain compromises hardware/software purchases, drops infected traps persisting stealthily extracting secrets or damaging continuity catastrophically triggered strategically in the least expected unforeseen ways.
FUN FACT
Because of the unavailability of skilled employees in the field of AI, cybersecurity, etc., 54% of the companies aren’t able to transform digitally.
Adopting Zero Trust Security
Conventional “castle and moat” network security assumes insider trust by all once the perimeter is breached. In contrast, zero trust architecture mandates stringent user/device verification continuously before granting least privileged access, minimally matching exacting needs, lowering risks profoundly consistently.
Engaging Employees Proactively

Empowering personnel to recognize subtle social engineering techniques, unsafe website links, and suspicious activity indicators helps workforce collectivists report threats early.
Maximizing incident response times, stemming breaches faster, and minimizing disruptions through unified collaboration containing exposures cooperatively once understood the Importance held organizationally thus individually then motivationally collectively lifetimes forward fearlessly.
Ongoing technical cybersecurity controls require equal workforce engagement, upholding diligent secure practices, and minimizing complacency around escalating phishing sophistication that, when one clicks, risks all downstream needlessly.
Therefore, education matters, and teaching diplomatically sensitive matters respectfully but earnestly consistently motivates maximal skills applied purposefully, minimizing risks significantly and moving forward fearlessly.
Continuous Monitoring and Improvement
Periodic maintenance keeps infrastructure optimizations continually aligned to evolving modernization needs as new equipment gets introduced and usage patterns shift based on market trends, favoring platforms that are preferred presently over alternatives that were viable decades prior but outdated woefully now. Steady diligence compounds advantages early.
Adopting an agile approach to technology management
Nimble tech-savvy committees oversee dynamic general controls, continuously matching information risks appropriately as external threat tactics shift evermore sophisticated but matched equally through ever-evolving countermeasures reinforced expertly by managed services partners.
Accelerating competitive advantages are hardly matched internally reasonably by most competitors struggling still a decade behind transitionally. Therefore, why, risks widen inequality profoundly until reconciled strategically forward analytically, seeking profound, meaningful discoveries rewarding.
But only available once understood analytically, lifetimes together fearlessly forward purposefully.
DID YOU KNOW
The Global Digital Transformation market was valued at $2.71 trillion in 2024 and is expected to reach $12.35 trillion by 2032.
Establishing regular maintenance and update schedules
Instead of hastily reacting to catastrophic failures or emergency security patches announced publicly and embarrassing high-profile companies frequently, planning prudent tech refresh roadmaps quarterly while automating firmware/software updates weekly ensures continuity risks are kept minimized, working supported platforms benefiting optimized constantly.
Conclusion
Optimizing complex technical environments that modern enterprises rely upon daily proactive assessments revealing risks, simplification opportunities, and capability gaps matched through cloud services, workflow automation, and integrated security controls. These improvements liberate resources, innovating higher while safeguarding continuity and bolstering data protections that give lasting competitive market advantages. Also, learn about Business with Facebook Marketing by reading this article.