Introduction to Deception Technology
According to the latest reports, only 4% of organizations feel confident in the security provided to users of connected devices and related software against cyberattacks.
This fact highlights a steady rise of online scams and virus infiltration. To counter it, the integration of deception technology is necessary to prevent valuable data loss.
Unlike traditional safety measures, the software system does more than just defend and damage control. It also deploys traps on attackers through its network through its complex methods. Also, know about Robots Dot To Dot Nattapong by reading this article.
This proactive approach helps detect threats early and offers significant advantages in response and recovery. This article will explore how deception technology works, its benefits, best practices, and its future trends. Also, learn about Cybersecurity Tips for Small Businesses by reading this article.
How Deception Technology Works
At its core, deception technology involves deploying decoys and traps within a network to attract and detect malicious activities. These decoys can mimic tangible assets, such as servers, databases, and applications, tricking attackers into engaging with false targets.
This illusion is designed to be convincing enough to divert the attacker’s attention from valuable resources. Alerts are triggered when an attacker interacts with a decoy, allowing security teams to respond swiftly and mitigate potential damage.
The artificially generated environment also provides an isolated space where ongoing attacks can be monitored in real time. It also offers a rich intelligence source without compromising tangible assets.
THINGS TO CONSIDER
The types of cyberattacks that can be prevented by deception technology are account hijacking, identity theft, IoT attacks, spear phishing, and lateral movement attacks.
The Benefits of Implementing Deception Technology
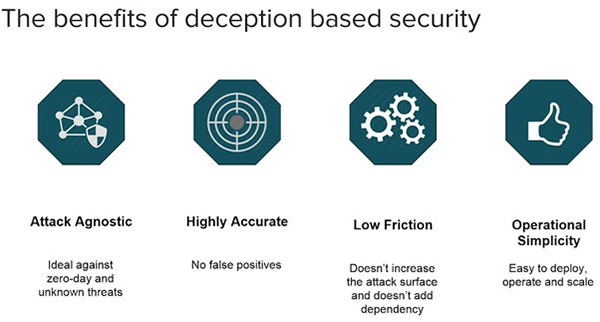
Integrating deception technology into your cyber safety strategy offers numerous benefits:
- It significantly enhances threat detection capabilities, providing early warnings of potential breaches before they can escalate. This early detection is necessary to minimize the damage and prevent further infiltration.
- It reduces response times by giving security teams valuable insights into attackers’ tactics and methods, enabling quicker and more informed decision-making.
- It is a valuable tool for gathering threat intelligence, helping organizations stay ahead of emerging threats and improve their defenses accordingly.
According to ZDNet, the adoption of advanced software is on the rise, with more organizations recognizing its potential to strengthen their security systems. IT consulting experts or services further enhance this trend by providing organizations with expert guidance on selecting and implementing the right software solutions tailored to their specific security needs, ensuring that their systems are effective and also resilient against emerging threats.
By creating a realistic but artificial environment, businesses can lure cybercriminals into a trap. This not only halts their progress but also provides a treasure trove of data on their methods and targets.
Integration with Other Security Measures
This highly effective deception tool functions optimally with additional security protocols. It may be used with more established defenses like firewalls, intrusion detection systems, and endpoint protection. It builds a multi-layered safety approach that makes it much harder for attackers to succeed.
This comprehensive strategy enhances overall network security and minimizes the risk of successful cyber-attacks. To create a defense-in-depth solid strategy, it can serve as an early warning system that supports other safety measures. With this layered strategy, many lines of defense are prepared to neutralize a danger, even if one is broken.
Real-World Applications of Deception Technology
Several businesses in various sectors have effectively used deception technology to safeguard their networks. For example, financial institutions use decoys to ensure sensitive customer data, while healthcare organizations deploy traps to protect patient records.
These sectors face stringent regulations and high stakes regarding data breaches, making this an invaluable tool. By using it, these companies may lessen the impact of any breaches by more efficiently detecting and responding to attacks.
Also, by analyzing attacker behavior isolated within decoy environments, businesses can better understand vulnerabilities and take proactive measures to fortify their defenses.
An article highlights multiple successful case studies illustrating the tangible benefits of this advanced software. Companies reported significant reductions in breach incidents and highlighted the ease of integrating Deception Technology with existing infrastructure.
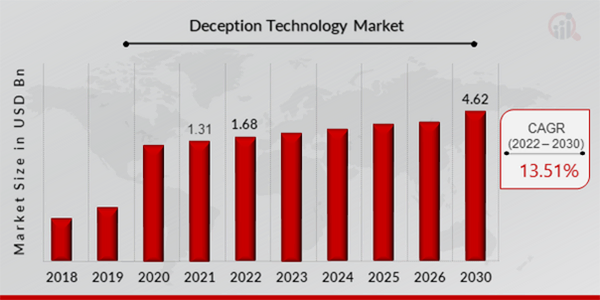
STATISTICS
The graph shows the growth and forecast of the deception technology market from 2018 to 2030.
Best Practices for Implementing Deception Technology
To maximize the effectiveness of deception technology, consider the following best practices:
- Deploy a variety of decoys that mimic genuine assets to detect attacks early. A diverse array of decoys will cover different facets of your infrastructure, making it more challenging for attackers to identify real targets.
- Update and maintain decoys regularly to ensure they remain convincing to attackers. The ever-changing cyber landscape necessitates continuous refinement of your complex tactics.
- Integrate this system with other preventive solutions to create a layered defense strategy. Coordination between various safety measures ensures a comprehensive shield against multiple attack vectors.
- Continuously monitor and analyze decoy interactions to gather valuable threat intelligence. The data collected from decoy environments can provide insights into emerging threats and help adapt your secure postures accordingly.
Future Trends in Deception Technology
As cyber threats continue to grow, so will deception technology. Future advancements include using artificial intelligence and machine learning to create more sophisticated decoys and automate threat detection.
AI-based decoys can learn from past interactions and adjust their tactics to appear even more genuine to intruders, improving the chances of engagement and detection.
Moreover, integration with other emerging advanced systems like blockchain may further enhance the capabilities of deceptive tools, making it an indispensable tool in the fight against cybercrime.
Blockchain can provide immutable records of decoy interactions, adding verification and traceability to similar strategies.
Final Thoughts
Deception technology offers a proactive method of threat identification and response, a paradigm change in cybersecurity. Organizations may significantly improve their safety by tricking attackers into falling traps and obtaining valuable information.
While it should not replace traditional protection measures, its integration into a comprehensive safety strategy can provide a formidable defense against the ever-growing landscape of cyber threats.
As software advances, the role of deceptive tools is poised to become even more significant, making it a cornerstone of effective cybersecurity practices for many years.
Also Read: What to Expect When Working with a Localization Agency