Cloud computing has become a billion-dollar industry and is used in almost every field. As highlighted by Forbes article, cloud computing offers improved analytics, business agility gains, and environmental efficiency. But is cloud computing available for everyone?
CEO of Salesforce.com once said, “The cloud services companies of all sizes, The cloud is for everyone. The cloud is a democracy.” This means that the cloud is not for a selected number of people it is for everyone but there must be some rules that need to be followed if you want to take full advantage of this service right?
In this article, we’ll talk about unwritten cloud computing rules that can make or break your strategy. You might be taking some steps wrong while accessing it so here’s a guide for you that will save up your time. Also, learn about Cloud Migration Mistakes by reading this article.
Contextualizing Cloud Strategies
A cloud strategy refers to intentionally planning a series of computing transitions from on-site systems to off-site cloud platforms. This matches evolving business goals around flexibility, analytics, sustainability, or collaboration, specifically over time.
Thoughtful strategies prevent rushed changes from risking significant disruption by carefully integrating targeted cloud capabilities without initially interfering with existing workflows unnecessarily. This allows for safely enhancing technology foundations supporting new efficiencies and innovations sustainably over longer-term roadmaps.
Various business motivations shape cloud approaches distinctly:
- Improving Responsiveness – Combined cloud infrastructure and built-in automation intrinsically improve responsiveness, adapting products, services, and internal processes faster, staying market-relevant against rivals.
- Unlocking Analytics – Utilizing dispersed datasets into shared lakes creates fuller enterprise-wide visibility, uncovering deeper customer insights, micro-trends, and operational analytics using scalable AI/ML modeling impossible previously.
- Environmental Sustainability – Cloud virtualization inherently consumes less of an ever-present physical footprint than traditional on-premise servers in the long term. Web-based options further reduce excessive provisioning and energy waste, cleverly aligning usage only to actual processing needs dynamically.
The Flexibility of Multi-Cloud and Hybrid Environments
Increasingly, strategically blending multiple cloud providers prevents over-dependence risks like unexpected regional service degradations or major vendor-wide outages due to their own software flaws or infrastructure instabilities.
Distributing environments across several vendors intrinsically increases workload reliability through redundancies, avoiding single points of failure that could otherwise halt operations entirely if relying on just one provider exclusively.
Look at this graph below that will show you at what rate Multi and Hybrid clouds are used.
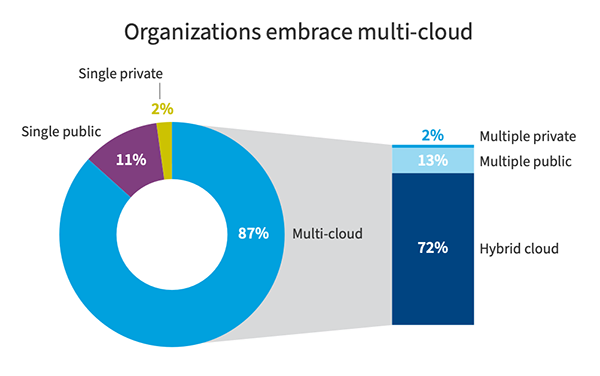
Standardized containers and orchestration interfaces also enable effortlessly shifting workloads between different cloud endpoints fluidly, always chasing optimal price-performance ratios and responding to shifting organizational demands rationally.
Cost-allocating usage cases to specific cloud vendors matching their particular differentiated strengths make sense rather than arbitrarily enforcing equal work distribution percentages without weighing unique capabilities thoughtfully.
Data Management Paradigms

While compiling expansive datasets creates invaluable enterprise-wide visibility for AI/ML predictive modeling, aimlessly ingesting volumes of information risks substantial waste and overhead.
Instead, the competence of IT support experts enhances this framework by consciously architecting data lifecycle management frameworks that maximize ROI, empowering organizations to efficiently manage data from creation to deletion.
This holistic approach ensures that valuable information is readily accessible and properly protected, significantly reducing operational risks. This framework, by providing specialized knowledge and resources, establishes that the systems are optimized for performance and security.
- Continually streaming pertinent business data into cloud data lakes, providing fresh analytics input for statistical models deriving actionable operational and customer insights.
- Responsibly applying analytical model outputs toward quantifiable business process improvements around efficiency, quality, or workflow automation opportunities.
- Automatically archiving older historical data to cost-efficient cold storage, minimizing recurring cloud hosting overhead.
Repeating sustains value perpetually instead of diluting potency, letting data analytics degrade outdated unused. This returns cloud investments over long-term planning horizons.
Cloud Performance Optimization Techniques
Beyond routine cloud cost configuration optimizations balancing server types and resource allocations sensibly, several innovative approaches further enhance hosted application performance and responsiveness:
- Geo-Distributed Deployments – Strategically position key application components and service instances at the nearest intended concentrated user base locations, minimizing physical transmission distances across nodes. This reduces communication latency, accelerating performance delivery and allowing for better globally localized digital experiences.
- Edge Computing Architectures – Offload front-facing user interface aspects onto localized distributed mini-server nodes at network edge locations while reserving heavier back-end computational number-crunching processes for core cloud resources and then relaying outcomes downstream. This splits processing duties optimally between cloud and edge, minimizing lag frustrations.
FUN FACT
The first ever company to adopt cloud computing was Salesforce.com in 1999 and then Amazon in 2002
- Auto-Scaling Rules – Rightsize cloud server capacity on demand by launching additional resources automatically only as surging user traffic volumes dictate, then winding down extra capacity during lulls. This optimizes overall hosting costs that are aligned dynamically to fluctuate and match real-world user demand patterns efficiently.
Leveraging cloud platform advantages in these ways targets optimizations beyond basics, truly boosting application speed and user experiences.
The Evolution of Cloud Security Postures

Imperva mentioned how traditional conventional network security controls continuously fail to safeguard fluid cloud environments with intrinsically increased risks from public access points. Instead, meeting the demands of evolving threats in cloud spaces requires adopting similarly more resilient and progressive security processes embracing cloud portability inherently:
- DevSecOps Mandate – Rigorously embed automated code vulnerability scanning and swift remediation processes seamlessly within continuous cloud delivery pipelines.
This bakes in consistent security scrutiny effortlessly throughout regular development cycles, rather than just assessing stability risks right before final deployment launches reactively. Identifying software flaws proactively during commits significantly mitigates attack surfaces exposed in production environments.
- Proactive AI Threat Detection – Employ intelligent machine learning algorithms capable of independently modeling baseline infrastructure performance and then continuously evaluating activity logs against those projected norms.
Differentiate honest anomalies from actual abnormalities accurately indicative of emerging malicious attacks autonomously. Cloud fluidity demands mitigating life threats rapidly in real-time through algorithmic pattern recognition rather than relying purely on reactive rule-based systems only flagging retrospectively known past attack signatures obliviously.
Navigating Compliance Challenges in Cloud Adoption
Especially within heavily regulated industries, static legacy compliance obligations always seem fixed. However, underlying cloud platforms advance so rapidly that uncertainty emerges, and they need help managing consistent compliance sustainably in the long term.
Just a few oversights introduced by continual cloud changes invite massive disaster through non-compliance risks realized too late.
Building Compliance Resilience Recommendations

- Thoroughly map both current and upcoming projected regulatory requirements beyond narrowly focusing just on technical specifications and also considering impacted privacy, security, and operational governance processes extensively.
- Adopt adaptive compliance review cycles, continually re-validating that existing control implementations still satisfy the latest revised industry regulations as frequent changes emerge. Set up automatic notifications for infrastructure teams, alerting them about any cloud service alterations affecting regulated data usage.
- Most critically, prioritize proactively integrating expected future compliance planning into initial cloud deployment designs, rather than attempting to retrofit inadequate band-aid fixes eventually. This helps to maintain infrastructure agility and scaling capacities appropriately down the road.
Emphasizing Continuous Learning and Adaptation
With exponential feature advancements emerging across cloud vendors annually, any one-time training regimen risks skill gaps, losing considerable operational optimization opportunities, and overlooks updated risk considerations quickly. Instead, purposefully maintain a perpetual elevation of in-house cloud expertise using:
- Immersive Self-Service Labs – Set up realistic interactive cloud sandboxes, facilitating hands-on experimentation and safely understanding platform intricacies through manipulations that are impossible to implement live initially when learning complex technologies. Virtual labs provide spaces that encourage the incubation of new skills without risks.
- Vendor-Specific Architect Certifications – Incentivize staff pursuing accredited specialized coursework and certifications formally validating expert-level architecture know-how specific to individual cloud providers. This tailors deployments following proven formula patterns, managing workloads most efficiently long-term per cloud.
- Attend External Cloud Conferences – Require staff to widen industry perspectives beyond internal corporate walls by participating in relevant cloud and edge computing conferences globally. Exposure to bleeding edge case studies and solution brainstorming sparks fresh tactical ideas brought back into local organizations, elevating support skills.
DID YOU KNOW?
In 2023 global cloud computing market was valued at $587.78 billion!
Conclusion
As outlined across keystone focus areas like data governance, compliance, multi-cloud leverage, and performance optimizations, numerous lesser-known details determine cloud success materially.
Mastering intricacies multiplies rewards through sustainable flexibility, actionable analytics, and governance structuring data. Whether dramatically enhancing insights, facilitating collaboration in real-time, or rightsizing computing for sustainability gains – bespoke strategies engineered to acknowledge essential principles will pay exponential dividends for years ahead, no matter which goals prioritize roadmaps today.
But don’t downplay mastering security and law enforcement basics, either. With the cloud now underpinning organizational progress across industries through versatility and accessibility, ensure foundations embed resilience first.